Welcome to Physical Security 101
What is physical security?
Let’s start with the definition found in the U.S. Army Field Manual 3-19.30:
Physical security is defined as that part of security concerned with physical measures designed to safeguard personnel; to prevent unauthorized access to equipment, installations, material, and documents; and to safeguard against espionage, sabotage, damage, and theft.
In fewer words, physical security deals with the physical measures used to protect people and property.
Risk assessment Fail to plan, Plan to fail …
Before we learn about those security measures we must first have a plan. At the very least we should know what to protect and from what. We start by doing a risk assessment.
After finishing the risk assessment we know the assets we must protect and the threats we could face.
Defense in Depth
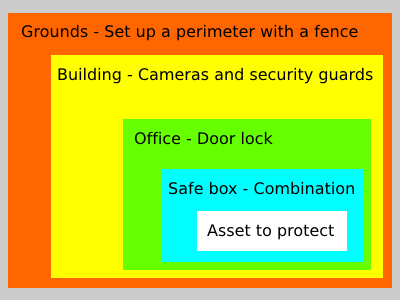
There exists no magical defense that would protect all assets from every threats. In fact, for every security measure that exists, a countermeasure can be found. That is why we never rely on a single measure to protect our assets. Like an onion has several layers, we will design a multilayer physical protection system by combining several security measures.
Defense in depth is the cornerstone of physical security.
The 4D security framework
In order to design an effective system, we will use the 4D security framework. It describes the four capabilities that a good physical protection system should have:
Deter – Prevent the attack
Detect – Be aware that an attack is in progress
Delay – Slow the attack and buy time for an appropriate response
Defend – Take action to counter the attack
So we have two powerful conceptual tools helping us protect our assets from threats. Defense in depth teaches us that we need several layers of security around our assets. The 4D framework reminds us of the effects that our physical security measures should produce.
Fundamental elements of physical security
We will now learn about some of the physical tools at our disposal in order to implement the 4D’s and protect our assets.
Barriers
 Primary capability: Deterrence
Primary capability: Deterrence
Secondary capability: Delay
Deterrence requires limits. These limits can be psychological or physical. In physical security we call these limits barriers.
Psychological barriers are a product of communication. They can be signs (DANGER Do NOT Enter), symbols (police badge), or the result of indoctrination. Good deterrents induce a fear of danger.
Physical barriers can be fences, walls, hedges, rivers, cliffs, safe boxes, or even a squad of riot police. Good physical barriers also provide a delay capability.
The best barriers are both psychological and physical, they can prevent and delay attacks.
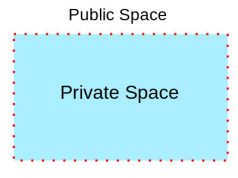
We use barriers to set up perimeters around the assets we want to protect. Most often we do this with fences or walls. We will need at least two perimeters. An outer perimeter and an inner perimeter.
We usually allow at least one point of entry/exit inside a perimeter, typically a gate or door, that becomes a part of the barrier.
Alarm systems
 Primary capability: Detection
Primary capability: Detection
Secondary capability: Deterrence
When deterrence is not enough and our perimeter has been breached, we want to be notified as soon as possible.
Alarm systems are comprised of two parts, a sensor and an alert mechanism.
There exists a variety of sensors that monitor movement, heat, sound, pressure, vibration, and a lot more. Advances in technology give us new kinds of sensors such as: cameras with motion detection, optical fiber sensible to pressure, glass break sensors.
The alert mechanism could be a siren, an email, a phone call, a database record, a panic button, any mechanism letting you know that an event has happened. Some alarm systems can be set to call your nearest police station when a sensor (or more) is triggered.
Alarms systems can give a deterrence capability and in some cases, delay as well.
In order for the physical protection system to be effective, the alarm system must alert someone (or something) that is able to assess the situation and take appropriate action. Otherwise it is useless for protection (but can aid investigation).
Access controls
 Primary capability: Delay
Primary capability: Delay
Secondary capability: Deterrence / Detect
Our alarm system has alerted us to the fact that something has happened. We need some time to assess the situation and respond to it.
Meanwhile the attack continues. We want to delay it so that the asset is safe as long as possible. That is why we need at least two perimeters.
Access controls are found at the access points, entry/exit, of perimeters. They allow or deny passage.
Access control examples: The lock on your front door, a card reader at the gate of a fenced parking, a police officer asking for ID to enter a crime scene, the combination of a safe box, a biometric scanner inside a nuclear facility.
Access points are most often the weakest point of a barrier (it is easier to go trough a door than a wall). We must make sure that only authorized personnel/items can enter the perimeter. This can be done by using keys, access cards, passwords, combinations, biometrics.
In case of forced entry, the access control mechanism should resist and buy time in order to allow a response before the asset is damaged or lost.
Security force
The most crucial part of physical security
Primary capability: Defend
Secondary capabilities: Deter, Detect, Delay
Now is time to respond to the attack and prevent damage or loss of the asset. The security force must intervene.
The goal of the responder is to stop the progression of the attack, by limiting the liberty of movement of the attacker, destroying its will and/or capabilities. Finally, the attacker can be apprehended if the situation permits.
Once the incident is resolved, its handling should be documented and later reviewed.
In civilized countries, citizens and corporations can call the police to respond to illegal attacks threatening their assets.
Private security force can be employed when no police can be called or to have a better response time, bigger force, specific response, etc.
Depending on location, hour, events and size of your security force, it takes time for it to respond. That is why it is important to know the reaction time of your security force when implementing delay measures.
You now know the basics of physical security:
– Risk assessment
– Defense in depth with multiple perimeters
– Deter, Detect, Delay, Defend
– Barriers, Alarms, Access Control, Security Force
This ends physical security 101.

































Dear sir,I sincerely found your journal to be highly informative and educative. its a reliable guide. Thanks
I personally think your article is fantastic! I agree with a lot of your unique views and am inspired to read more. I truly like your writing style. Thank you.
This is good training.